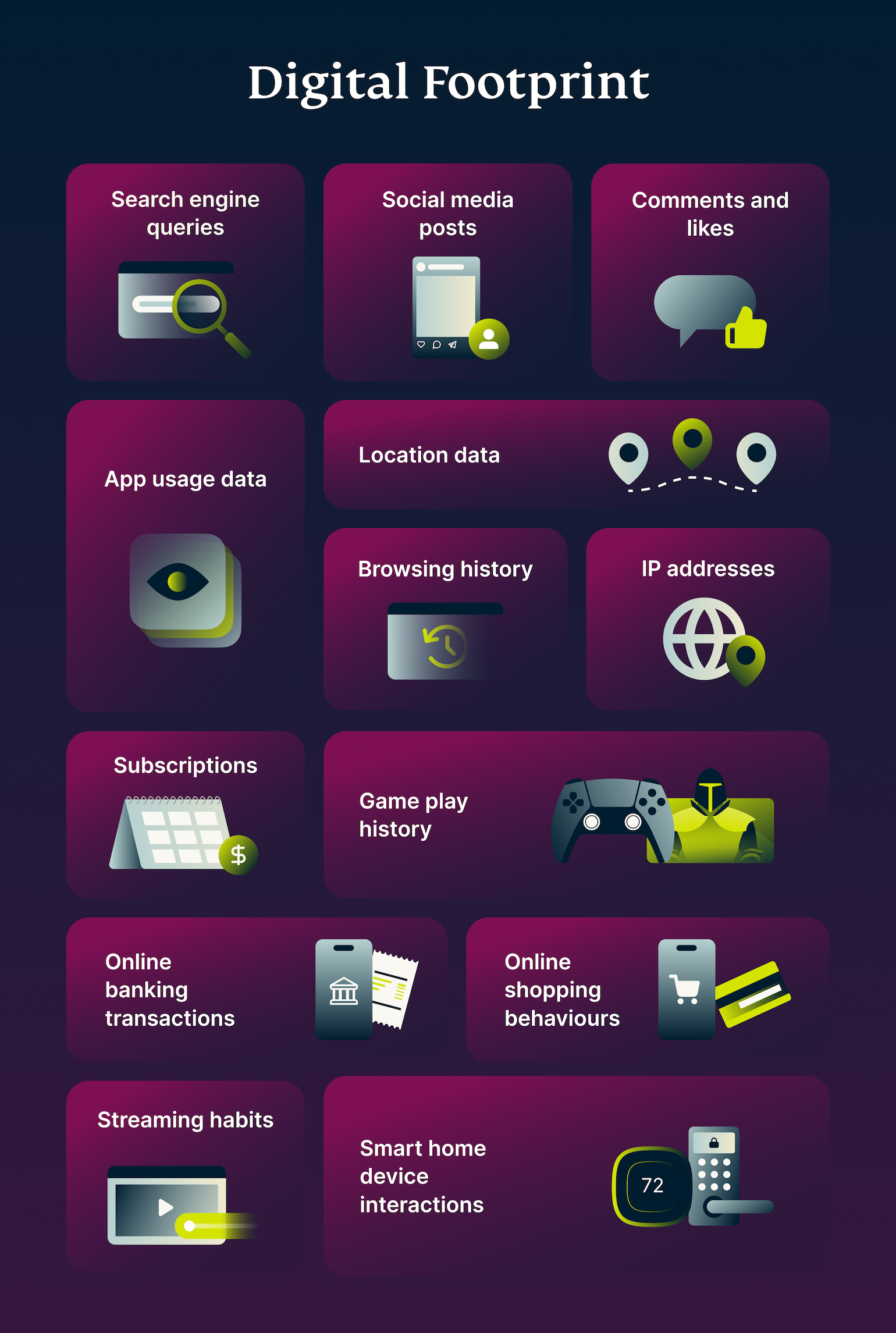
With the rise of social media and online platforms, every click and keystroke contributes to our digital footprint. This collection of online actions, such as social media updates, online purchases, and web searches, can significantly impact our personal and professional lives. Understanding the nature and impact of our digital footprints helps us manage and protect our online personas.
Unzipping your digital footprint
Your digital footprint is the result of all your activities on the internet.
It can also be broken down into two main categories: active and passive. Active digital footprint is the data you intentionally share, such as social media updates, photos, and personal information, while the passive digital footprint is the data collected without your explicit consent, like browsing history, IP addresses, and location data from mobile devices.
Real-life risks resulting from your digital footprint
Now that we know the trail of data we leave behind every time we go online, let’s dive into how it can have repercussions in our daily lives.
Various real-world impacts can arise if someone uses the data from our social media posts, online shopping behaviors, browsing history, IP addresses, comments and likes, and metadata from photos and documents.
- Identity theft: Details such as your full name, date of birth, and address from social media posts and online profiles can be exploited by cyber attackers. This information can be used to impersonate you, leading to significant financial losses, damaged credit scores, and a lengthy recovery process.
- Job opportunities: Employers often review candidates’ social media profiles during the hiring process. Inappropriate posts, controversial comments, or a lack of professionalism online can negatively affect your chances of securing a job.
- Personal safety: Sharing your location through social media updates or metadata in photos can put your and your loved ones personal safety at risk. Cyberstalkers and other malicious actors can use this information to track your movements and target you, leading to real-world dangers.
- Social engineering attacks: Cybercriminals use information from your browsing history, IP addresses, and social media activity to craft convincing phishing messages. These attacks can lead to data breaches, financial loss, and compromised personal information.
- Online scams: Your digital footprint can make you a target for various online scams, from fake investment opportunities to fraudulent online stores. If your digital footprint for example shows you are interested in investing, the likelihood of financial scams working may be higher.
- Reputational damage: Inappropriate or controversial online behavior can damage your reputation. This can affect personal relationships, career prospects, and even social standing within your community. Comments, likes, and even seemingly harmless posts can come back to haunt you.
- Data breaches: Storing personal information online increases the risk of data breaches. When companies or services you use experience breaches, your data can be exposed and misused by cybercriminals.
- Loss of privacy: Extensive sharing of personal information can lead to a loss of privacy. This makes it easier for others to monitor your activities and potentially misuse your data.
- Blackmail: Cybercriminals may use your private information to extort money or favors from you. They can threaten to release sensitive data unless their demands are met.
By understanding these real-world impacts, you can take proactive measures to protect your digital footprint and mitigate potential risks.
Technical threats and how to protect yourself
Now, we reach the critical question: how do attackers transform your online activities into tools for exploitation? By understanding their methods, you can better protect your digital and real-world identities from these threats.
Metadata exploitation
Metadata in your digital files, like photos and documents, can expose sensitive information such as your location, the device you used, and the time the photo was taken. Geotagging, which embeds geographical data in media files, can reveal your precise location. Hackers and malicious actors can use this information to track your movements and learn more about your habits.
How to protect yourself:
- Remove metadata: Before sharing photos, use tools like ImageOptim for Linux/Mac/Windows, or Snapseed for Android/iOS to strip out metadata. Remember to always download software from reputable and trustworthy sources.
- Share wisely: Limit the amount of personal information included in digital files.
- Check privacy settings: Ensure your devices and apps aren’t automatically sharing your location.
IP address tracking
Your IP address can reveal your approximate location and track your online activities across different websites. Threat actors can use this information to learn more about you or to target you with specific attacks.
How to protect yourself:
- Use a VPN: A VPN app can hide your IP address and encrypt your internet traffic.
- Keep software updated: Regularly update your devices and software to protect against vulnerabilities.
Read more: With ExpressVPN, your IP changes for every site
Browser fingerprinting
Browser fingerprinting collects details about your device, such as browser type, plugins, and screen resolution, to create a unique profile. This makes it easier for websites and trackers to follow you online.
How to protect yourself:
- Privacy-focused browsers: Use browsers that offer anti-fingerprinting features, such as Brave.
- Install privacy extensions: Add browser extensions that block fingerprinting scripts, like uBlock Origin.
- Clear browsing data: Regularly delete cookies and browsing history to reduce tracking.
Social engineering and phishing
Phishing and social engineering attacks trick you into revealing personal information, such as passwords or credit card numbers, by pretending to be legitimate entities. Hackers often use details from your digital footprint to craft these convincing messages.
How to protect yourself:
- Verify sources: If you receive an unusual request, check the sender’s email address and make an effort to confirm the sender’s identity.
- Enable multi-factor authentication: Add an extra layer of security to your accounts.
- Use spam filters: Employ filters to detect and block phishing emails.
- Stay skeptical: Be cautious of unsolicited messages asking for personal information.
- Educate yourself: Learn about common phishing and social engineering tactics. One very nice resource is the Phishing quiz by Google that is interactive and offers valuable tips.
- Confirm requests: Always confirm the legitimacy of requests for sensitive information, even if they seem to come from trusted sources.
Read more: How to spot common red flags in phishing emails
Malware and ransomware
Malware is software designed to harm your device or steal data, while ransomware locks your files and demands payment to unlock them. Cybercriminals may use information from your digital footprint to tailor malware attacks.
How to protect yourself:
- Install antivirus software: Use reliable antivirus and anti-malware programs.
- Keep software updated: Regularly update your operating system and applications to fix security holes.
- Avoid suspicious links: Don’t click on links or download attachments from unknown sources.
Read more: Frightening reality: You can buy ransomware as a service
Data harvesting
Data harvesting involves collecting extensive data from various sources without your consent, often for targeted advertising or political campaigns. Information from your digital footprint can be pieced together to create a detailed profile.
How to protect yourself:
- Limit data sharing: Be mindful of the personal information you share on social media.
- Adjust privacy settings: Set privacy controls on social media and other platforms to restrict who can see your data.
- Opt-out: Use opt-out features on websites and services to limit data collection.
Man-in-the-middle attacks
These attacks occur when someone intercepts communication between two parties without their knowledge, often on unsecured networks. Information from your digital footprint can help attackers exploit these vulnerabilities.
How to protect yourself:
- Use encrypted connections: Stick to HTTPS websites (most browsers will warn you before visiting an HTTP page) and end-to-end encrypted messaging apps like WhatsApp and Signal.
- Use a VPN: A VPN will ensure that even if you visit HTTP sites, your traffic is encrypted from your device to the VPN server, protecting you from man-in-the-middle attacks.
- Avoid public Wi-Fi: Use a VPN when you must access the internet on public networks, which could be unsecured.
- Secure your network: Protect your home network with strong passwords and encryption.
Read more: Why use VPN for HTTPS sites?
Knowledge is safety
By understanding these real-world impacts and technical threats, you can take proactive measures to protect your digital footprint and mitigate potential risks. Be mindful of the information you share online, use privacy tools and settings, and stay informed about the latest digital security practices.
Take action now:
- Review your social media privacy settings.
- Use a VPN.
- Install anti-virus software.
- Regularly update your devices and software.
- Educate yourself about phishing and other online threats.

30-day money-back guarantee