-
Managed DNS: Your complete guide to understanding and implementation
DNS is a foundational component of every organization’s IT infrastructure. A reliable DNS service not only ensures fast query resolution and minimizes downtime, but it also strengthens resilience ag...
-

What is a subnet? A complete guide to subnetting, VPNs, and network security
A subnet is a key concept in networking that involves dividing a network into smaller segments. This allows networks to be structured so devices and services can communicate efficiently and securely. ...
-

What is 128-bit encryption, and is it still secure in 2025?
128-bit encryption remains a cornerstone of online security, protecting everything from VPN traffic to mobile apps. It’s widely used and has never been reported to have been cracked. But with ongoin...
-

What are network protocols? A complete guide
Incalculable quantities of data flow from device to device and network to network on a daily basis, and every single transmission follows a very specific set of rules and standards. Those rules and st...
-
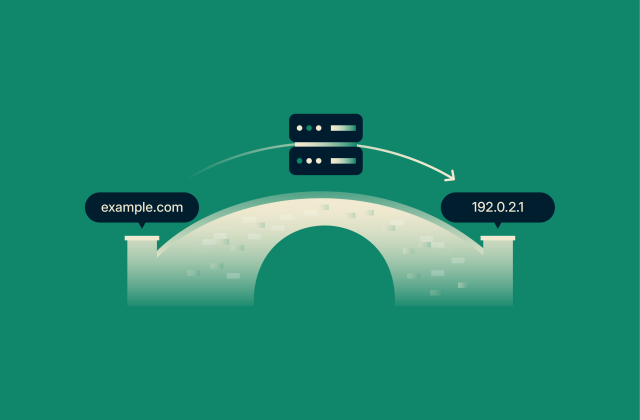
Nameserver: The complete guide to setup, management, and troubleshooting
Nameservers are essential for any functioning website or email domain. Without proper nameserver configuration, emails wouldn't reach their destinations, and visitors would encounter loading errors wh...
-

Zeus virus (Zbot malware): What it is and how to stay protected
The Zeus virus is best known for fueling large-scale financial cybercrime and stealing banking credentials. Although the original Zeus virus is no longer active, it spawned numerous variants that rema...
-
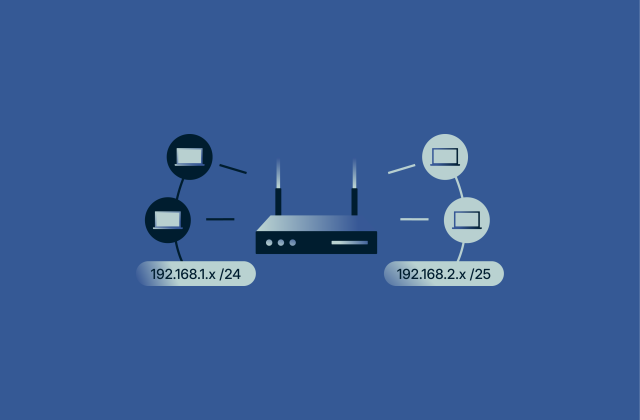
What is a subnet mask? Why it matters for your network
Every device on a network needs a way to know where information should go. Without clear rules, data would move blindly, causing confusion and slowdowns. Subnet masks are one of the tools that make ne...
-

How to block a TikTok account: A step-by-step guide
TikTok can be fun, but it also has people you might not want around. Maybe someone keeps dropping comments you don’t like, maybe they flood your DMs, or maybe their videos just won’t stop showing ...
-

Connected but no internet access: Why it happens and how to fix it
Getting a message stating that you’re connected but have no internet access can be frustrating. If your network is fine, why won’t websites load? It’s often unclear what has caused this error me...
-

How to delete your WhatsApp account (step-by-step guide)
Whether you’re done with WhatsApp for good or just taking a break, the process of deleting your account is relatively quick and easy. This guide will show you exactly how to delete or uninstall your...
Featured




