What is an IP stresser, and how do DDoS booters work?
IP stressers are tools used to test how well a network can handle high volumes of traffic. While they can serve a legitimate role in cybersecurity, using them to intentionally overwhelm a network, which is known as a distributed denial of service (DDoS) attack, turns them into DDoS booters.
This guide covers everything you need to know about IP stressers and booter tools. You’ll learn what these tools are, how they differ, and whether it’s ever legal to use them. We’ll also walk you through the best ways to protect yourself or your business from DDoS attacks. Let’s dive in.
Understanding IP stressers and booters
 IP stressers are tools primarily used for testing network resilience, but they can also be misused in the wrong hands. Booters, on the other hand, are almost solely used to launch malicious DDoS attacks. Before we get into all the ways they can be used for harm, let’s break down the key differences between IP stressers and booters and the different roles they play in cybersecurity.
IP stressers are tools primarily used for testing network resilience, but they can also be misused in the wrong hands. Booters, on the other hand, are almost solely used to launch malicious DDoS attacks. Before we get into all the ways they can be used for harm, let’s break down the key differences between IP stressers and booters and the different roles they play in cybersecurity.
What is an IP stresser?
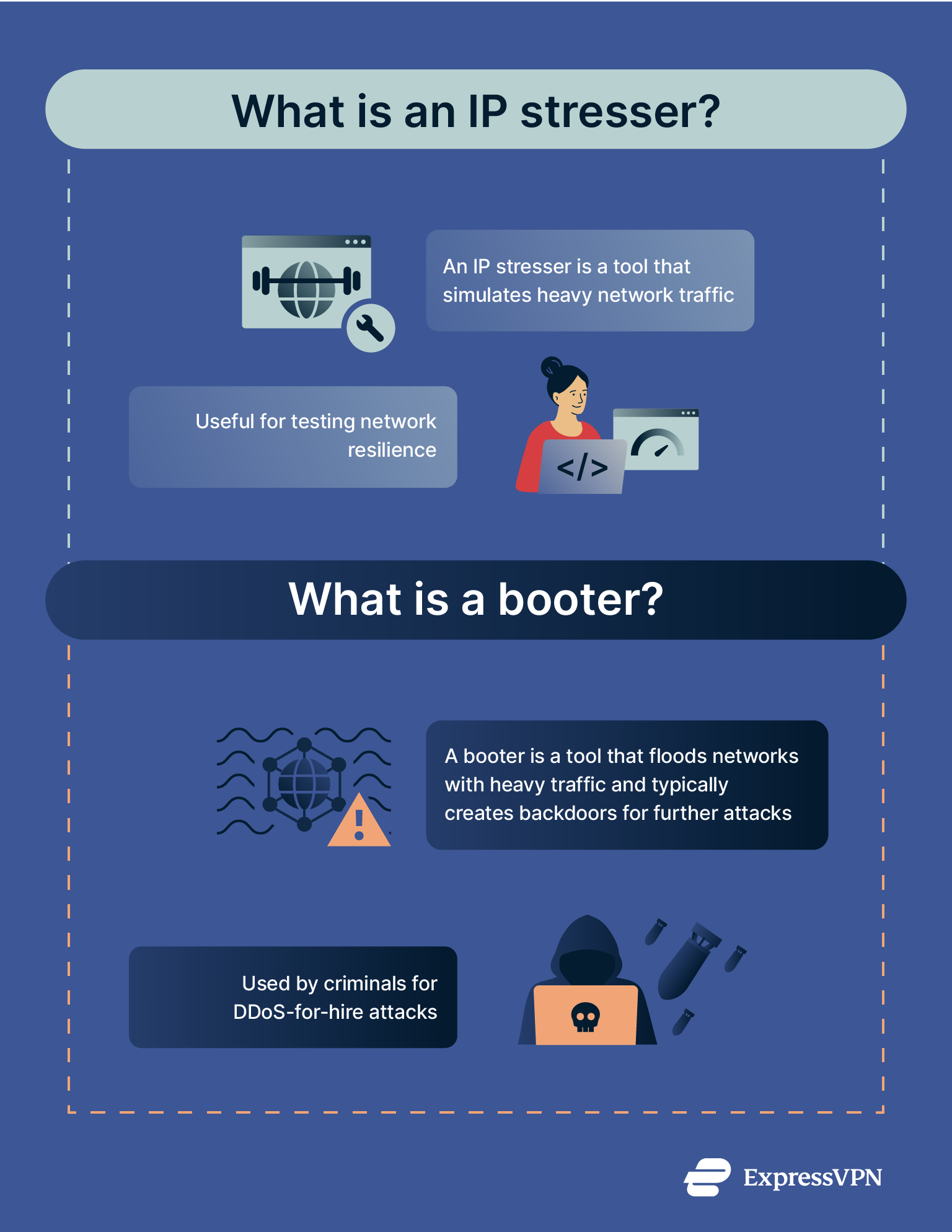
An IP stresser is a tool designed to simulate heavy traffic on a target system, usually to test a server’s ability to withstand high loads. It’s typically used by IT professionals who want to assess the strengths and weaknesses of a network and identify areas for improvement.
While IP stressers have legitimate uses, they can also be exploited for malicious purposes. In the wrong hands, they can be used to flood a target network with traffic, effectively launching a DDoS attack.
How does an IP stresser work?
An IP stresser works by sending large volumes of traffic to a target IP address, overwhelming its resources. The goal is to simulate high-traffic conditions to identify weak points in the network that may need improvement or protection. Think of an IP stresser as a tool that simulates a DDoS attack or, if used maliciously, actually launches one.
What is a booter (DDoS booter)?
A booter, or DDoS booter, is a type of DDoS-for-hire service that sends massive amounts of uncontrolled traffic to a network to intentionally overload it. Typically, one individual or group operates the service, while others pay to launch attacks through a booter website. Booters are almost exclusively used for criminal purposes and are illegal in most countries.
The cybercriminals who run booters use large networks of “zombie” devices (devices that have been compromised by hackers through malware or by exploiting vulnerabilities) for their attacks. These devices are grouped together into a botnet, which then targets uncontrolled network traffic to the victim.
DDoS booter services are often marketed as tools for testing a network’s defenses, but in reality, they’re not suitable for legitimate testing. Unlike IP stressers, which simulate high-traffic conditions in a controlled environment, booters carry out unregulated attacks designed to disrupt or damage a network.
How does a booter service work?
A booter service combines a variety of network attack methods, including botnets (networks of private computers infected with malware and used for attacks without the users’ knowledge) and Domain Name System (DNS) amplification (where an attacker uses a DNS server to flood the target with traffic).
Typically, a criminal pays a booter operator to attack a company or individual, allowing them to disrupt their services without needing any technical expertise.
Booters have existed for a long time and have evolved significantly over the years. In the past, hackers had to operate their own servers and route their attacks through proxies. This limited their DDoS capabilities because they could only create as much traffic as their individual device could handle. Now, they can take advantage of cheap and easily accessible botnets to launch far more powerful attacks.
The tool floods a victim's network with malicious traffic designed to overwhelm their defenses (firewall and network infrastructure) and sever their internet connection, usually with the click of a button from a main booter panel. Many booters also come with software designed to create backdoors into the victim's network, making it easier to launch follow-up attacks later.
What’s the motivation for DDoS attacks?
Key economic and psychological motivations behind DDoS attacks include:
- Financial gain: The most obvious reason? The attacker is hired to launch an attack on a specific target. It’s also common for a hacker to DDoS a victim and demand a ransom payment in exchange for stopping the attack.
- Reputational damage: Booter operators will try to harm a person or company’s reputation by relentlessly DDoSing them to cause network outages. This can prevent a person from reaching their remote job or damage a business by blocking new sales for however long the outages last.
- Ideology: Some attackers are driven by ideology or beliefs. They might target organizations or governments whose actions they oppose, whether politically, socially, or environmentally. This is especially true of hacktivists, who use DDoS attacks to protest causes like censorship, animal cruelty, or environmental harm.
- Revenge: Some people launch DDoS attacks over personal grievances (against schools, ex-employers, rivals, or even gaming opponents).
- For fun: Some people will DDoS a target just for fun. Sometimes, it’s simply to test their technical expertise or a victim's defenses, without any deeper motivation.
- Corporate sabotage: There have been cases of businesses hiring hackers to sabotage their corporate rivals with destructive DDoS attacks. For example, notorious hacker Daniel Kaye was hired by a rogue employee working for Cellcom to DDoS the competitor company, Lonestar, in an attack that ultimately crashed Liberia’s entire internet.
- Cyber warfare: State-sponsored hackers, or threat actors working on behalf of a nation, may use DDoS attacks to disrupt critical infrastructure or gain political and military advantages.
- Diversionary tactics: Sophisticated attackers sometimes use DDoS attacks as a smokescreen, diverting attention while they carry out more targeted operations like breaching systems or deploying malware.
Legal status of IP stressers and booters
You’re probably wondering: are IP stressers and booters legal? And what happens if you use one? While the laws vary from country to country and can get quite complex, most of the time booters are completely illegal, while IP stressers are legal under very limited conditions.
When is it legal to use an IP stresser?
IP stressers are only legal when used for authorized network testing. This means you can only stress test your own network or one where you have explicit, written permission from the owner. Using them on third-party systems without consent is illegal. For the most part, only IT professionals should be using IP stressers.
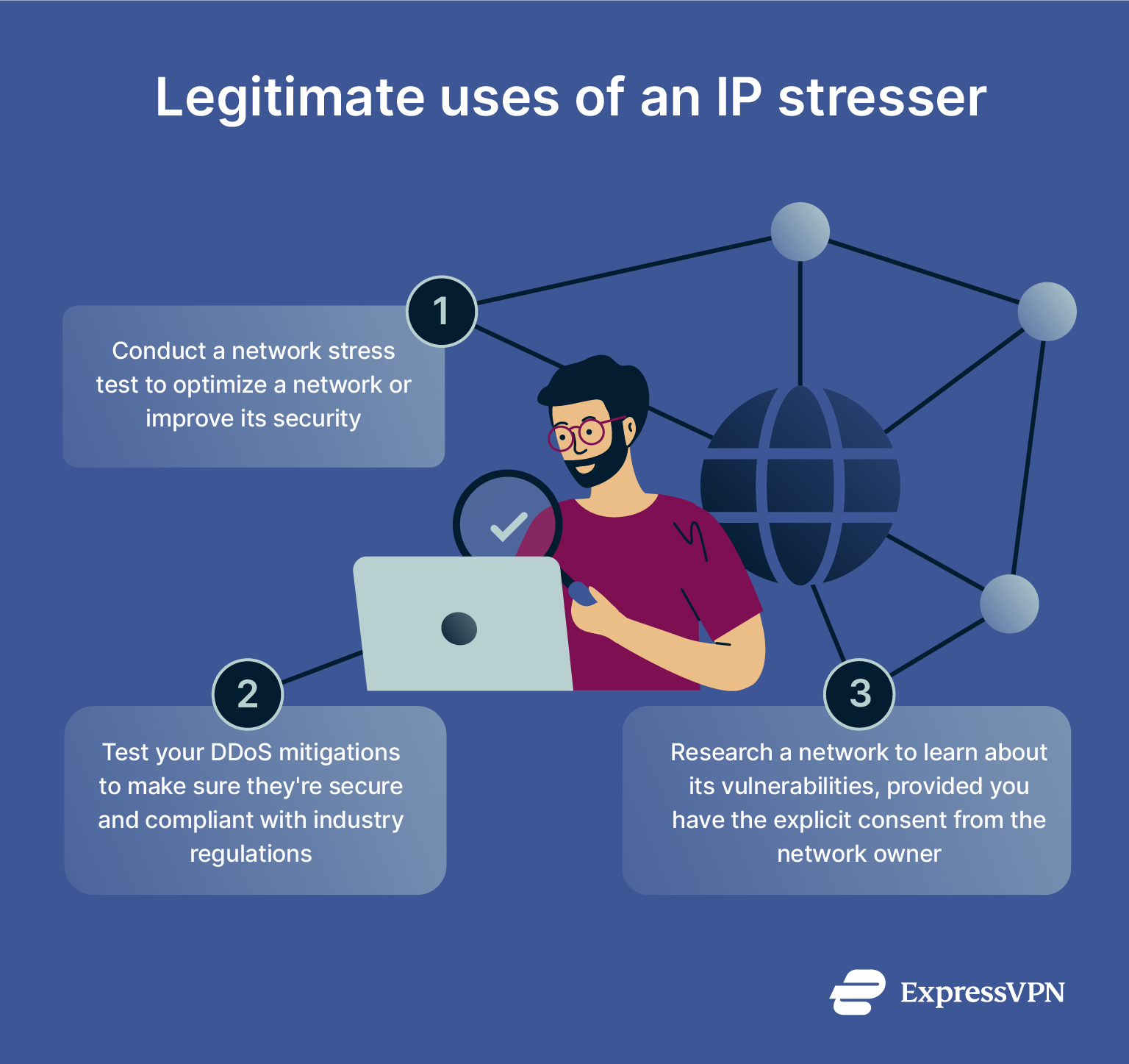
Legitimate uses of IP stressers
IP stressers have several legitimate benefits for experts or IT professionals who want to engage in network testing and who have the proper consent from the network owner. In these circumstances, IP stressers can be used to:
- Conduct a network stress test: Professionals can use IP stressers during company audits to test for vulnerabilities within the network. The stresser will inform them of how the network will behave during real-world high-traffic situations. The data gathered from the stresser is used by the network owner to optimize services or improve security.
- Test your DDoS mitigations: IT teams may simulate DDoS attacks to evaluate the strength of their mitigation tools. This is useful for meeting compliance requirements or preparing for real attacks that could result in financial loss or service downtime.
- Cybersecurity research: Researchers or ethical hackers might use a stresser on a network to gather research about its vulnerabilities.
Consequences of using an IP stresser or booter illegally
Penalties vary by country, but in general, using an IP stresser or booter without permission can lead to significant fines, prison time, and expensive civil lawsuits. In the US, there is even a law that can ban someone from using a computer if they’re found guilty of a felony related to cybercrime.
Booters aren’t impossible to trace. Take Sergiy P. Usatyuk, an Illinois resident who was arrested for his role in a DDoS-for-hire service and sentenced by the U.S. Department of Justice (DoJ) to 13 months in prison. Detectives followed breadcrumbs he left behind, like PayPal transactions and IP address access logs, to discover his real identity.
And because DDoS attacks often affect systems in multiple countries, attackers can face international prosecution. Law enforcement agencies worldwide actively pursue individuals involved in DDoS-for-hire schemes, meaning, in some situations, the same hacker can face criminal charges in every country where their tools were used.
For example, Daniel Kaye is a prolific hacker known for DDoSing several major companies. He was caught in the U.K. and extradited back to Germany, where he was charged for hacking Deutsche Telekom. After serving his sentence, he was brought back to the U.K. to carry out his sentence for DDoSing Lonestar.
Laws and regulations against booter services
Countries like the U.S., U.K., and many EU nations have strict laws against booter services. For example, in the U.S., using or selling booters violates the Computer Fraud and Abuse Act (CFAA), while the U.K.'s Computer Misuse Act criminalizes unauthorized attacks on computer systems.
The risks of using IP stressers and booters
IP stressers and booters pose serious risks, not just to the victims of DDoS attacks, but also to the people using these tools. From hidden malware to potential criminal charges, here’s what makes them so dangerous.
Security threats and cybercrime risks
Free or unlicensed IP stressers and booters frequently come bundled with malware like spyware, backdoors, or keyloggers. These tools can be used not just to launch attacks but also to steal sensitive information from the user.
Booter software should always be considered malicious. It's illegal in most countries, and free versions are almost guaranteed to contain harmful code.
How IP stressers are misused for DDoS attacks
Although IP stressers can be invaluable for legitimate network testing, they are often used to launch DDoS attacks against businesses, individuals, and game servers. Over time, a single threat actor might launch hundreds of thousands of attacks, costing companies millions.
Attackers frequently combine stressers with techniques like IP spoofing (disguising the sender’s IP address) and DNS amplification. They use a multi-layered approach to cause as much damage as possible.
Why booter services are difficult to trace
Booter operators often hide behind proxies, VPNs, IP spoofing, and cryptocurrency payments. Many run their operations on the dark web.
These measures make it difficult, but not impossible, for law enforcement to track them. But for the average person, tracing the attacker’s real location is virtually impossible.
Legal alternatives for network stress testing
Instead of using IP stressers or booters, organizations can choose trusted penetration testing tools for legal network assessments. Many cybersecurity firms offer licensed stress testing services that are compliant with all local laws and industry standards.
If a company wants ISO/IEC 27001 certification (the internationally recognized standard for information security management systems), it’s strongly recommended that they use penetration testing services as part of their risk assessment process.
Even though some IP stressers are legal, their use is restricted. It’s always safer to use vetted, professional tools and services.
How to protect against DDoS and IP stresser attacks
Safeguarding against DDoS and IP stresser attacks requires a mix of proactive security measures, real-time monitoring, and dedicated DDoS protection software. Here’s a quick breakdown of how to protect your systems.
Best practices for DDoS protection (for individuals)
 Gamers, streamers, and online content creators can be highly vulnerable to booter-related attacks. For example, many streamers face consistent DDoS attacks from their online haters, usually with the intent of taking them offline or preventing them from making money over long periods of time.
Gamers, streamers, and online content creators can be highly vulnerable to booter-related attacks. For example, many streamers face consistent DDoS attacks from their online haters, usually with the intent of taking them offline or preventing them from making money over long periods of time.
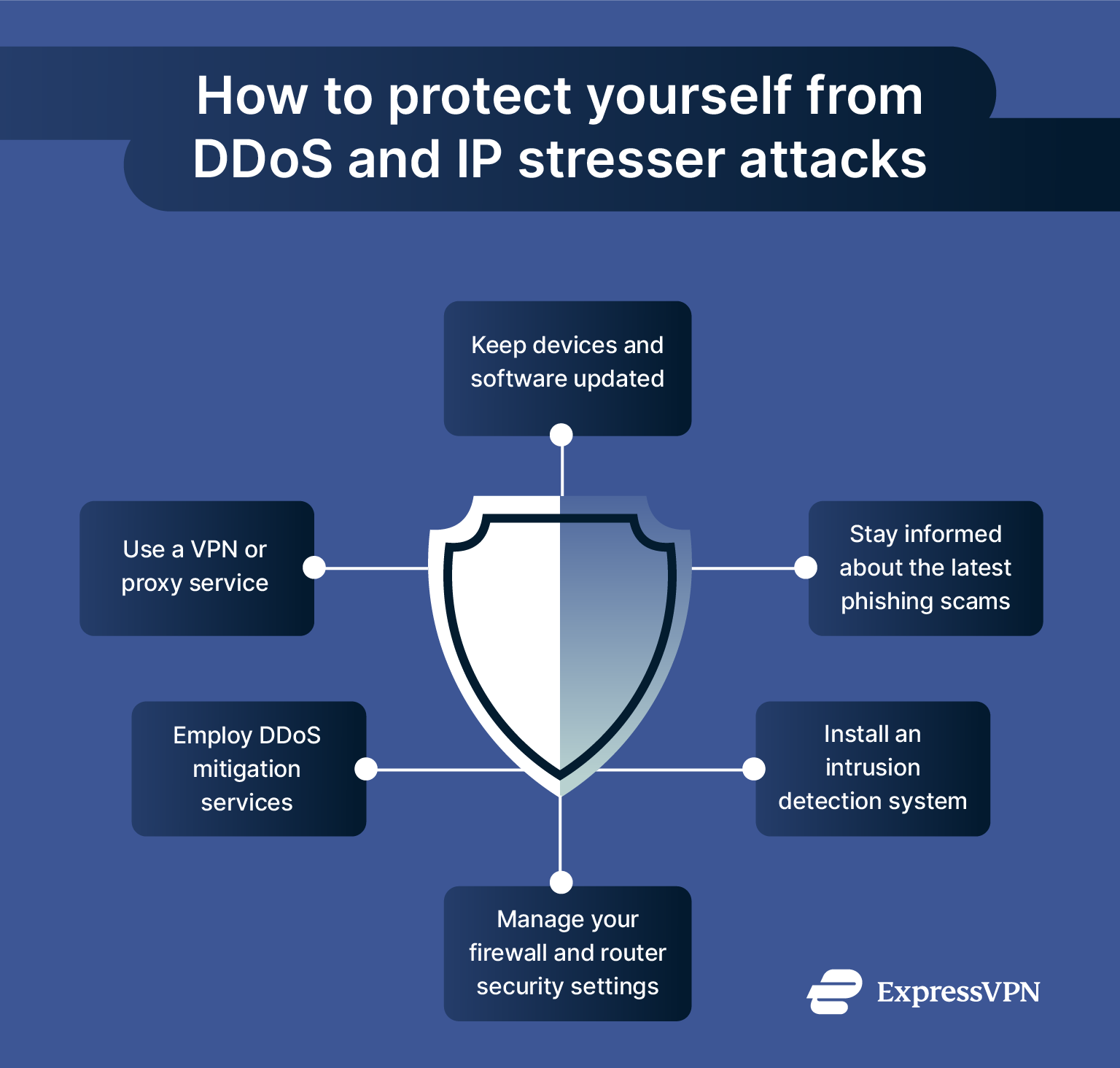
To protect yourself against DDoS attacks:
- Enable DDoS protection (if gaming/streaming): Many gaming platforms and ISPs offer DDoS protection features or allow you to change your IP address if attacked.
- Use a good firewall and customize your firewall and router security settings: Properly configured firewalls monitor incoming and outgoing traffic, blocking unauthorized access and potential threats.
- Avoid sharing your IP address: Don’t reveal your IP on public forums, game servers, or streaming platforms. A VPN is particularly good at stopping you from accidentally leaking your IP address.
- Stay informed about phishing attempts: Hackers often use phishing or social engineering to trick individuals into revealing their IP addresses. Make sure you stay up-to-date on the latest phishing scams and how to avoid them.
- Install an intrusion detection system (IDS): IDS tools provide real-time threat monitoring and can detect and respond to potential threats before they escalate.
- Employ DDoS mitigation services: These tools filter out malicious requests before they reach your network, minimizing damage during an attack.
- Keep your devices and software updated: Regularly update all software, operating systems, and devices to patch known vulnerabilities and strengthen your overall defense. OS-level vulnerabilities, if left unpatched, can enable network traffic to crash or deadlock your device, making it crucial to install the latest patches without delay.
Best practices for DDoS protection (for businesses)
 Protecting a business or organization is much trickier than defending yourself. Hackers constantly probe for vulnerabilities within companies, so you need to aoply a multi-layered security strategy to protect your organization. In extreme cases, DDoS attacks can force a company to permanently shut down. Here’s what you can do to protect your business:
Protecting a business or organization is much trickier than defending yourself. Hackers constantly probe for vulnerabilities within companies, so you need to aoply a multi-layered security strategy to protect your organization. In extreme cases, DDoS attacks can force a company to permanently shut down. Here’s what you can do to protect your business:
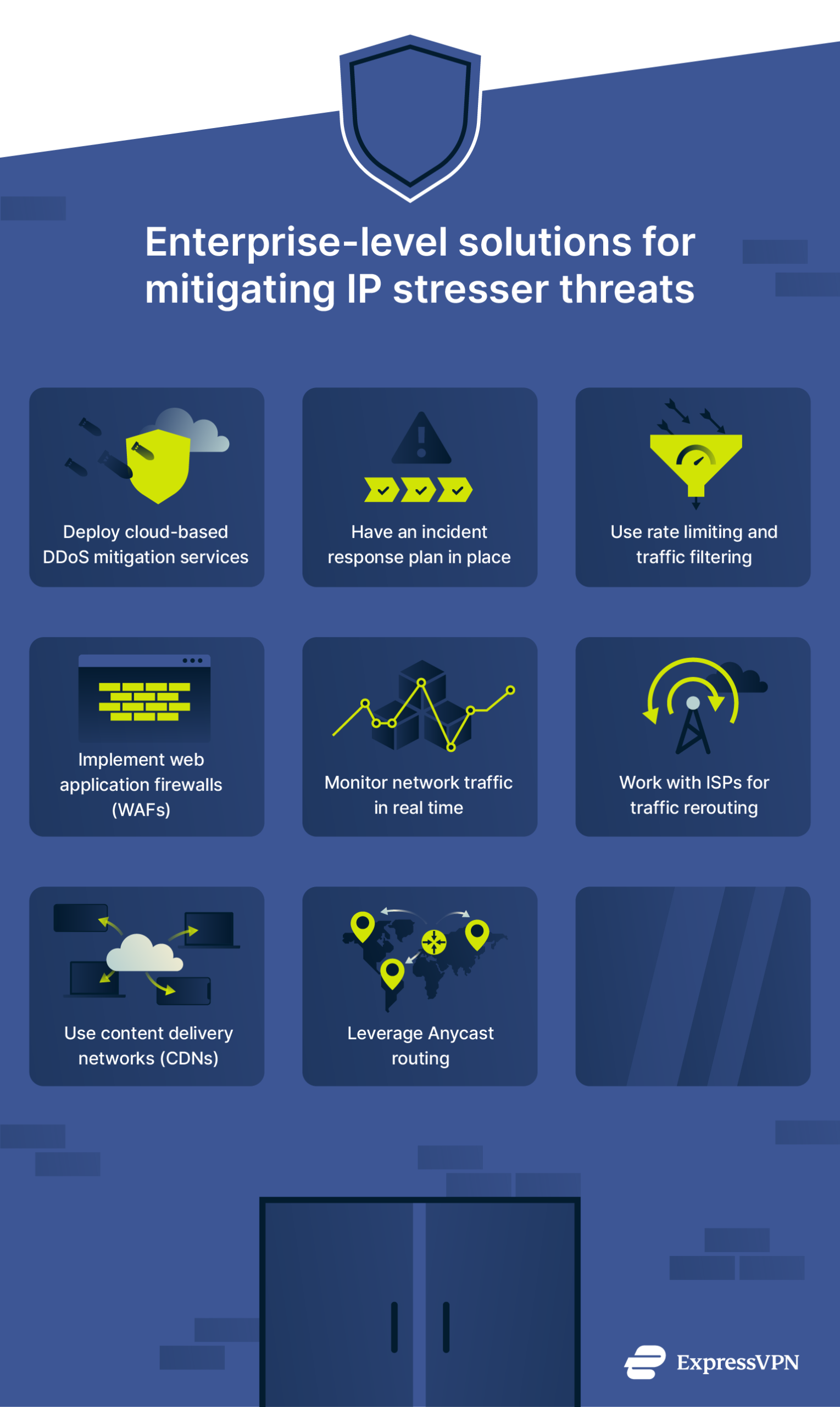
- Deploy cloud-based DDoS mitigation services: Use a reputable and effective DDoS mitigation service to help filter and absorb attack traffic before it reaches your network.
- Have an incident response plan in place: You should prepare automated responses and recovery plans to minimize downtime during an attack.
- Use rate limiting and traffic filtering: Configuring firewalls and network policies to limit abnormal traffic spikes can help mitigate attack impact.
- Implement web application firewalls (WAFs): WAFs protect layer 7 (the application layer, where most DDoS attacks target) by actively monitoring and blocking suspicious traffic in real time
- Monitor network traffic in real time: Using intrusion detection and prevention systems (IDPS) can help detect suspicious activity and prevent attacks on the network level (level 3) and above, blocking it before anything else happens.
- Work with ISPs for traffic rerouting: Some ISPs offer DDoS scrubbing services to divert malicious traffic away from critical infrastructure. This is specific to your ISP, so they may not have these protections, but it’s always worth checking.
- Use content delivery networks (CDNs): Enterprise-grade CDNs help distribute traffic and reduce the strain on your primary servers by routing requests to their own network of servers. Additionally, many CDNs have built-in security features, including DDoS mitigation systems, to help protect against large-scale attacks.
- Leverage Anycast routing: Distributing traffic across multiple servers avoids single points of failure by having backup systems in place, much like having multiple entrances to a building, so if one is blocked, people can use another. This can help mitigate the impact of DDoS attacks but should be combined with other tactics, such as traffic filtering or a DDoS mitigation service, since it only redirects traffic and doesn’t block malicious traffic.
If this sounds complicated, it is. Large organizations should work with qualified IT professionals to set up secure configurations and ensure they’re using the right tools for their needs.
Why a VPN is essential for DDoS protection
A VPN hides your real IP address, making it much harder for attackers to target you directly with IP-based threats like booters or DDoS attacks. By masking your true location, a VPN reduces your exposure and makes it harder for hackers to identify or reach your network.
VPNs also encrypt your internet traffic and route it through secure servers, protecting your data from interception or manipulation. Some VPNs, like ExpressVPN, even include built-in DDoS protection on their servers, which can block smaller-scale attacks before they ever reach you.
That said, a VPN alone won’t stop all DDoS threats. If a hacker manages to uncover your real IP address or targets the network you’re connected to, you’ll still need dedicated DDoS protection tools. A VPN can hide your location, but it can’t prevent an attack that’s already underway.
How ExpressVPN prevents IP tracking and spoofing
When you connect to ExpressVPN, your real IP is replaced with the IP of the VPN server, hiding your network from potential attackers. ExpressVPN uses shared IP addresses, meaning multiple users connect through the same server, making it much harder to trace activity back to any one person.
Additionally, ExpressVPN’s servers have built-in DDoS protection, helping to absorb the impact of small-scale attacks. While it may not block larger, sustained attacks, it can help reduce the damage.
Finally, ExpressVPN’s kill switch will automatically cut off internet access if the VPN gets disconnected, preventing your real IP from being exposed.
What to do if you suffer a DDoS attack

DDoS attacks require immediate attention, as they can deal heavy network damage if not dealt with swiftly. Here’s what to do if you’re targeted:
- Identify the attack and review your defenses: First, look at what’s happening. Then, gauge the scope of the attack to determine if your protection is adequate. Review your current defenses, including your security response plan, DDoS mitigations, and DNS security.
- Alert your ISP: After confirming the DDoS attack, alert your ISP. Many service providers offer some DDoS mitigation tools that can help minimize the harm caused during the attack.
- Follow your or your organization's incident response plan: Everyone on a team needs to be correctly following the company’s incident response plan, if it has one. This way, everyone is on the same page regarding communications and strategies to counter DDoS attacks.
- Deploy your DDoS mitigation tools: Deploy the mitigation tools that are available to you, including always-on DDoS security tools, cloud-based DDoS mitigations, or any unique software that you or your organization employs.
- Log everything: Keep logs of everything that happens. These can be used in the future to help find vulnerabilities or by law enforcement to find and arrest the hacker behind the attack. However, note that keeping records of everything can amplify the stress on your network in the event of a large attack.
- Report the attack: Finally, report the event to the appropriate authorities for your region so they can begin investigating the hacker.
Case studies and real-world examples
Here are some notable instances of IP stressers and booter services being used in DDoS attacks and the legal consequences that followed.
Notorious DDoS attacks involving IP stressers and booters
Hackers have used stressers and booters for thousands of attacks around the world for a variety of reasons, including driving a profit, disrupting specific services, or as part of broader online hacktivist campaign. Specific examples include:
- DDoS attack on Spamhaus (2013): A huge and infamous DDoS attack on Spamhaus, an international organization that tracks and publishes lists of IPs and domains associated with malicious activity. The attack was perpetrated by a Russian-based anti-Spamhaus group, but the main culprit turned out to be a teenage hacker in London. He was sentenced to 240 hours of community service.
- vDOS DDoS-for-hire service (2012-2016): One of the most infamous DDoS-for-hire services, vDOS launched over 2 million attacks against targets worldwide. Run by two Israeli teens, the service earned hundreds of thousands of dollars in profits before law enforcement shut it down. The operators were sentenced to community service and fined, with authorities recovering more than $175,000 in profits.
- WebStresser (2018): With over 136,000 registered users and millions of attacks launched, WebStresser was one of the most prolific DDoS-for-hire platforms in history. Multiple perpetrators were arrested, and 250 users of the service also faced legal action for the damage they caused.
- Quantum Stresser (2012-2018): Another major booter service, Quantum Stresser had over 80,000 users and was used to launch more than 50,000 attacks in 2018 alone. The operator of Quantum Stresser was caught in 2018 and sentenced in 2020 to 4-5 years of probation and 6 months of community confinement. His light sentence was due to his poor health.
- DDoS attacks on Russian media (ongoing): After Russia invaded Ukraine, hacktivists began launching DDoS attacks against Russian media companies and government websites.
- Widespread attacks on gaming platforms (ongoing): Gaming services like Xbox Live, PlayStation Network, and Steam have long been targets of DDoS attacks. Hackers also target specific game providers, like when they disrupted Blizzard Entertainment’s servers and blocked access to games including Overwatch 2 and Diablo 4 in 2023.
FAQ: Common questions about IP stressers and DDoS booters
Can law enforcement trace IP stresser attacks?
When is it legal to use an IP stresser?
What are the legal consequences of operating a booter service?
What are the best defenses against booter attacks?
A VPN can also mask your IP, making it harder for attackers to find you in the first place, though it won’t help once an attack is in progress.
What are the most common types of IP-based attacks?
What types of attacks can booter services perform?
How does IP spoofing relate to DDoS attacks?
How do hackers use stressers?
Booters, however, are usually preferred because they’re specifically built to deliver massive volumes of uncontrolled traffic. Usually, if a hacker wants to launch a DDoS attack, they’ll use a booter.
Are there free IP stresser tools available?
What should I do if I am targeted by an IP stresser attack?
Don’t give the hackers any money. If they are blackmailing you, there’s no guarantee they’ll actually stop once you pay.
Can a VPN protect me from DDoS attacks?
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN