What is post-quantum cryptography?

Quantum computers might still feel like something out of sci‑fi, but they’re improving fast, and one day, they could break the encryption schemes we rely on to keep the internet secure.
That’s where post‑quantum cryptography (PQC) comes in. It’s all about creating quantum‑resistant algorithms that can stand up to these future threats.
In this guide, we’ll look at what PQC is, why it matters right now, and what steps organizations can take to prepare for the quantum era before today’s encryption schemes become outdated.
Why post-quantum cryptography matters today
Encryption has come a long way from simple secret codes to the complex algorithms we rely on now, but it’s always been an arms race between those building secure systems and those trying to break them. Today, a new challenger, quantum computing, could change everything.
Most of the internet relies on public‑key encryption like Rivest–Shamir–Adleman (RSA), which is secure because factoring huge numbers is incredibly difficult, and Elliptic Curve Cryptography (ECC), which relies on the complexity of elliptic curve math. These are rock-solid against traditional computers, but quantum computers could solve those problems much faster, potentially breaking these encryption schemes wide open.
We don’t know exactly when powerful quantum computers will arrive (maybe in a few years, maybe in a few decades), but most experts agree it’s a matter of when, not if. That’s why it’s crucial to start preparing now, long before today’s encryption schemes become vulnerable.
The rising urgency of cryptographic modernization
Governments and organizations aren’t waiting for quantum computers to become a real-world threat; they’re preparing now. Why? Because cybercriminals can steal encrypted data today and decrypt it later once quantum technology matures.
This “harvest now, decrypt later” tactic is a big deal because some data stays sensitive for decades. Think financial records, government secrets, or personal credentials. A breach of that information could have consequences ranging from reputational damage and regulatory penalties to national security risks.
Governments around the world are already publishing roadmaps and mandates for quantum readiness. And because switching to post‑quantum encryption is a complex, years-long process, early preparation is essential to keep long-term data secure and stay compliant.
What “crypto-agility” means in the quantum era
Crypto‑agility is the ability to quickly swap cryptographic algorithms across your systems with minimal disruption. This adaptability is crucial because both standards and threats are evolving, and we don’t yet know which post‑quantum algorithms will stand the test of time.
Building modular, algorithm‑agnostic systems gives organizations the flexibility to adapt fast and stay secure as the quantum landscape changes.
How current cryptography works and its limitations
To understand why quantum computing is such a big deal, it helps to look at how today’s cryptographic systems work and why they could be at risk.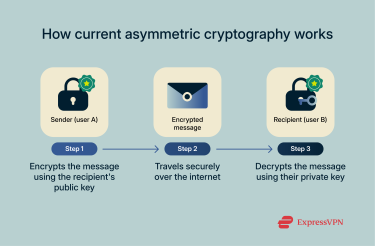
The role of public-key cryptography in modern security
Most secure communications today, from online banking to e‑commerce transactions, rely on public‑key cryptography. This method uses a pair of linked keys:
- A public key (shared openly) to encrypt or sign data
- A private key (kept secret) to decrypt or verify it
Algorithms like RSA and ECC generate these keys and handle the encryption and decryption. They’re based on mathematical problems that classical computers can technically solve, but only with an unrealistic amount of time. For example, even the world’s fastest supercomputer would take billions of years to factor a 2048‑bit RSA key.
These public-key cryptography algorithms are the backbone of digital certificates, Transport Layer Security (TLS) / Secure Sockets Layer (SSL), and key exchange mechanisms, which are the very tools that keep data safe across the internet.
Real-world vulnerabilities in current systems
Quantum computers, however, work in a completely different way than classical computers. This breaks the assumptions on which classical cryptography is built.
For example, a powerful enough quantum computer using Shor’s algorithm could factor a 2048‑bit RSA key in just a few hours, which is something impossible for today’s machines. That means many of the encryption methods we rely on for digital security could one day be obsolete.
Core post-quantum cryptographic approaches
As the quantum threat grows, researchers are building new cryptographic methods designed to stay secure even against powerful quantum computers. Here are the main approaches being developed:
- Lattice-based cryptography: This approach is based on solving lattice problems, a type of math problem that’s extremely hard for both classical and quantum computers. Many of the leading National Institute of Standards and Technology (NIST)‑standardized post‑quantum algorithms, including Module Lattice–Based Key Encapsulation Mechanism (ML-KEM), formerly known as Kyber, are lattice‑based because of their strong security and practical performance.
- Hash-based signatures: These use cryptographic hash functions to create digital signatures. Because reversing hash operations is computationally infeasible (even for quantum computers), this approach is considered highly secure.
- Code-based cryptography: This relies on the difficulty of decoding random linear error‑correcting codes without the secret key. Currently, no efficient quantum algorithm (including Shor’s) can solve this problem, making it a strong candidate for post‑quantum security.
- Isogeny-based techniques: These methods use isogenies, mathematical mappings between elliptic curves, to generate secure keys and signatures. They have the advantage of smaller key sizes compared to many other post‑quantum approaches. However, they’re still less mature and are being actively researched and evaluated.
Post-quantum resilience of symmetric key cryptography
Symmetric cryptography uses the same secret key to encrypt and decrypt data. Both parties share this key ahead of time. Advanced Encryption Standard (AES) is one of the most common symmetric algorithms, securing Wi‑Fi networks, VPN traffic, and encrypted files.
The good news is that symmetric cryptography is less vulnerable to quantum computers than public‑key systems. That’s because it doesn’t rely on mathematical problems such as factoring large numbers (used in RSA) or solving elliptic curve equations (used in ECC), problems that quantum computers can solve much faster using Shor’s algorithm.
For symmetric encryption, the main quantum attack is Grover’s algorithm, which speeds up brute‑force key guessing but doesn’t break the encryption outright. It only cuts the effective security of a key in half.
The fix is simple: use longer keys. For example, moving from a 128‑bit AES key to a 256‑bit AES key maintains strong security even in a post‑quantum world.
How organizations can prepare for quantum threats
Preparing for quantum threats requires a strategic, phased approach across both technical and organizational layers. Below are key elements organizations should consider.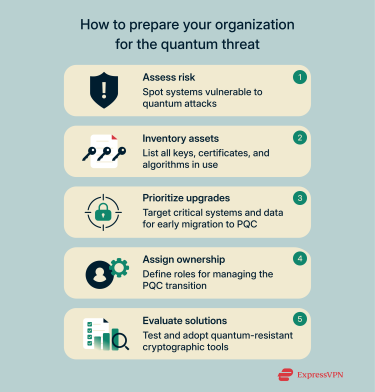
Building a cryptographic asset inventory
Start by assessing risk. Identify which cryptographic systems are most exposed to quantum threats. Then map out all your cryptographic assets, including algorithms, keys, certificates, and devices. This gives you a clear view of where quantum‑sensitive components exist and what will need upgrading.
Prioritizing systems and migration phases
Rank systems based on data sensitivity, exposure to quantum threats, and lifespan. Focus on critical areas like key exchange protocols and digital certificates first.
Use a phased migration strategy, often with hybrid cryptography, where classical and post‑quantum algorithms run side by side for compatibility and security.
Testing and validation pipelines
Test PQC tools early in controlled environments to uncover hardware, software, or performance issues. Many cryptographic libraries, such as liboqs, already support NIST’s post‑quantum algorithms (including the newly finalized standards), making hands‑on experimentation easier.
Early testing helps build crypto agility, so your systems can quickly adapt if vulnerabilities are discovered, reducing the risk of disruption when new standards are mandated.
Aligning governance and policy
Quantum‑safe transitions need policy and governance changes too. Organizations should:
- Align with the National Institute of Standards and Technology (NIST) and International Organization for Standardization (ISO) standards.
- Define clear internal rules for algorithm choice, key management, and interoperability.
- Include quantum‑safe requirements in procurement and requests for proposals.
- Foster crypto agility so algorithm updates are quick and painless.
Collaboration between IT, security, compliance, and leadership teams is essential to drive adoption and maintain accountability.
Training and internal communication
Successful PQC migration depends on people as much as technology. Provide targeted training for engineering and security teams on algorithm selection, migration paths, and implementation challenges.
Ensure clear internal communication. Assign roles and keep IT, security, and procurement teams informed about quantum‑safe requirements and migration progress.
Technical challenges and open questions
Below are key issues that remain open and require attention as PQC adoption grows:
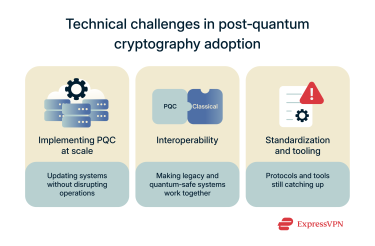
Challenges in implementing PQC at scale
Rolling out PQC across an entire organization, or even a national infrastructure, is a huge task. Every affected system, from servers and cloud services to IoT devices, needs updated cryptographic algorithms. That means:
- Updating or replacing software and hardware.
- Making sure operations aren’t disrupted.
- Dealing with potential performance hits, as some PQC algorithms need more processing power, which is especially challenging for low‑power or resource‑constrained devices.
Interoperability between legacy and quantum-safe systems
Another big challenge is making legacy systems and quantum‑safe systems work together. Right now, many organizations are using hybrid approaches, where classical and post‑quantum algorithms run side by side during the transition. This helps maintain compatibility but also adds complexity:
- Designing and testing hybrid systems.
- Handling key exchanges and digital certificate updates without introducing new security gaps.
- Ensuring data remains protected during and after migration.
Limitations in current standardization and tooling
Even with NIST’s new PQC standards, the ecosystem isn’t complete. Some cryptographic use cases and protocols aren’t fully covered yet, and PQC integration tools are still maturing. For example:
- Hybrid‑PQC support exists, but only on a limited number of platforms.
- Custom-built applications often have even fewer options, making full, seamless PQC deployment a work in progress.
How global standards shape quantum-safe security
As the quantum threat draws closer, cryptographic standards for PQC are playing a central role in shaping cybersecurity strategies and guiding secure migration efforts.
NIST’s post-quantum cryptography standardization process
Since 2016, NIST has led global efforts to develop quantum‑resistant cryptographic standards.
After years of open evaluation and testing by researchers worldwide, NIST finalized three PQC standards in August 2024:
- Module Lattice–Based Key Encapsulation Mechanism (ML-KEM), based on CRYSTALS‑Kyber, for encryption and key encapsulation.
- Module Lattice–Based Digital Signature Algorithm (ML-DSA), based on CRYSTALS‑Dilithium, for digital signatures.
- Stateless Hash–Based Digital Signature Algorithm (SLH-DSA), based on SPHINCS+, as a backup digital signature option.
A fourth signature algorithm, Fast Fourier Lattice–Based Compact Signatures over NTRU (FALCON), is also being standardized, expected as Federal Information Processing Standard (FIPS) 206.
In March 2025, NIST also selected Hamming Quasi-Cyclic (HQC), a code‑based algorithm, as a fifth PQC standard expected to be finalized by 2027.
National Security Memorandum 10 (NSM-10) explained
In May 2022, President Biden signed National Security Memorandum 10 (NSM‑10) to accelerate the U.S. government’s adoption of PQC. It requires federal agencies to:
- Conduct cryptographic risk assessments.
- Inventory existing cryptographic assets.
- Begin adopting NIST’s finalized PQC standards.
This directive highlights the urgency of early preparation and sets clear timelines to unify and speed up the federal response to quantum computing threats.
Evaluating PQC-ready vendors and products
With cryptographic standards now solidifying, more vendors are marketing their products as “quantum‑safe” or “PQC‑ready.” Organizations should carefully evaluate these claims:
- Identify critical vendors that handle hosting, storage, data processing, or software distribution.
- Review vendor cryptographic transition plans, certifications, and roadmaps.
- Ask about support for NIST algorithms, hybrid modes, and crypto‑agility for future updates.
- Assess testing maturity and migration support to ensure smooth adoption.
Tools to help you and your apps get ready for the quantum future
Organizations should take advantage of the growing ecosystem supporting the shift to PQC to streamline their transition to quantum-safe encryption.
Recommended open-source PQC libraries
Experiment with quantum‑safe implementations using mature, open‑source libraries:
- Open Quantum Safe (liboqs): A leading open‑source library for PQC that supports NIST‑selected algorithms and integrates with Open Secure Sockets Layer (OpenSSL) and Open Secure Shell (OpenSSH). It’s been used by AWS, IBM, SandboxAQ, and ExpressVPN for early implementation and testing.
- Bouncy Castle: A well‑established cryptography library for Java and .NET that now supports NIST’s finalized post‑quantum algorithms, including CRYSTALS‑Kyber, CRYSTALS‑Dilithium, and SPHINCS+. It enables hybrid TLS and certificate workflows, making it easier to integrate quantum‑safe cryptography into enterprise environments.
Tools for cryptographic discovery and inventory
Discovery and inventory tools automate identifying cryptographic algorithms, keys, certificates, and devices used across networks and systems. They help map the scope of migration, detect outdated or vulnerable algorithms, and prioritize high-risk assets.
Examples include Keyfactor Command and Venafi’s Trust Protection Platform, both widely used for continuous cryptographic asset management and compliance.
Official migration guidelines from NIST and industry bodies
Migration doesn’t need to be guesswork. Official resources provide best practices, risk management frameworks, and step‑by‑step guidance for assessing current cryptographic assets, planning migrations, and validating implementations:
- Quantum-Readiness: Migration to Post-Quantum Cryptography published by the National Institute of Standards and Technology (NIST), the National Security Agency (NSA), and the Cybersecurity and Infrastructure Security Agency (CISA).
- The PQC Migration Handbook produced through a joint effort by Dutch government and research organizations
- Next steps in preparing for post-quantum cryptography issued by the National Cyber Security Centre (NCSC), a government organization in the U.K.
FAQ: Common question about post-quantum cryptography
What is quantum-safe encryption?
Quantum-safe encryption refers to cryptographic methods that remain secure even against attacks from powerful quantum computers. This includes post-quantum cryptography (PQC) algorithms designed to withstand quantum attacks and hardware-based methods like quantum key distribution (QKD).
Can existing systems be upgraded to PQC?
Yes, existing systems can often be upgraded to support post-quantum cryptography (PQC), usually through hybrid approaches that run classical and post-quantum algorithms simultaneously during the transition. However, some devices, especially low-power or legacy hardware, may require upgrades or replacements.
What are the first steps to crypto-agility?
The first steps to crypto-agility are building a complete inventory of where and how cryptography is used in your organization and establishing strong governance practices. This includes documenting algorithms, keys, certificates, protocols, and hardware across your systems, as well as setting clear policies for cryptographic selection and management. From there, focus on flexible implementation and lifecycle automation to support future updates as needed.
What are the finalized NIST PQC standards?
The National Institute of Standards and Technology (NIST) has finalized three post-quantum cryptography (PQC) standards: two lattice-based algorithms (CRYSTALS-Kyber and CRYSTALS-Dilithium) and one hash-based algorithm (SPHINCS+). These standards form the foundation for quantum-safe encryption and digital signatures, with additional algorithms currently under review.
How is post-quantum cryptography different from quantum cryptography?
Both are approaches to achieving quantum-safe security. Post-quantum cryptography (PQC) is software-based and uses new mathematical algorithms designed to resist attacks from quantum computers, replacing vulnerable public-key methods.
Quantum cryptography, on the other hand, is hardware-based technology that leverages the principles of quantum physics, particularly quantum key distribution, to exchange encryption keys securely, detecting eavesdropping through quantum effects.
In other words, PQC strengthens the encryption itself using new math, while quantum cryptography secures the key exchange process by physically detecting any interception attempts.
How long does migration typically take?
Migrating to post-quantum cryptography (PQC) is a long-term process that can take many years. For context, it took nearly two decades to fully deploy modern public-key infrastructure across industries.
Given that some experts estimate cryptographically relevant quantum computers could emerge within 10 to 15 years, organizations must begin preparing now to ensure systems are ready well before the threat materializes.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN