Your YouTube history exposed: Researcher identifies inherent security flaw in video streaming


This post was originally published on March 22, 2017.
While researching how Internet Service Providers (ISPs) could optimize their services to improve users’ video-watching experiences, cyber-security expert Ran Dubin realized that ISPs could ascertain more than just watch quality—they could, if they wanted to, determine the precise video titles their users were watching.
Dubin’s method differs from usual monitoring approaches in that it only analyzes traffic patterns, whereas traditional monitoring techniques look at unencrypted data, exploit flaws in the protocol, or analyze individual packets.
Although YouTube uses encryption to secure your data, Dubin explained to ExpressVPN, anyone watching your network could determine exactly what you’re watching—but there is a way you can protect yourself.
Mapping streams to patterns
Dubin told ExpressVPN,
“I found out that all the streams actually have a very distinguished pattern. And those patterns can be identified.”
Your browser does two things when you use YouTube to stream videos:
- It opens an encrypted channel with YouTube through which all data is transferred.
- It requests and receives small sections of video at a specific quality, depending on the speed of your network connection.
Despite being encrypted, the encoding mechanisms generate enough data for sophisticated passive observers to piece together what you’ve been watching. In the wrong hands, this data could easily be sold or otherwise used to target and discriminate against virtually anyone.
Each video has a unique, traceable signature
Dubin’s research found that while your video is loading, anybody observing the connection—like your ISP, a hacker tapping your Wi-Fi network, or a government agency—can follow the distinct patterns of encrypted data flows over time.
This pattern exists because the videos are downloaded in ‘chunks,’ creating peaks and silence in the traffic flow. By analyzing the number of bits-per-peak—determined, for example, by the number of colors or quick movements in that chunk of video—a signature for the video is created, allowing it to be uniquely identified.
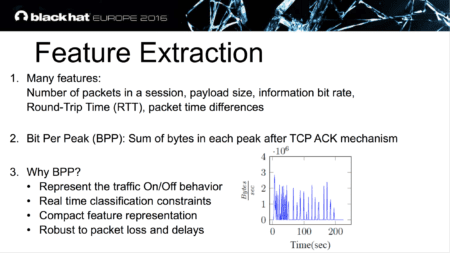
Ran Dubin, Amit Dvir, Ofir Pele, and Ofer Hadar. “I Know What You Saw Last Minute - The Chrome Browser Case.” Lecture, Black Hat Europe 2016, London, November 3, 2016.
To match each pattern to a video, the passive observer would need to have a precompiled list of all the videos they want to monitor. While it would be difficult to compile a list of all the videos available on YouTube (given that about 300 hours of new content are uploaded every minute), it is possible to compile such a list for popular videos—or videos of interest.
Potential for privacy abuse
Although determining what video you’ve watched is no small feat, this passive analysis could become very troublesome if groups with the wrong motives were able to determine if you’d watched any video on one of these precompiled lists:
- Videos related to a specific politician
- Videos related to a specific resistance movement
- Informational videos about certain health conditions
- Videos related to smoking cessation or other addiction
It raises the possibility that anyone could be targeted, cohorted, or discriminated against by their government, ISP, or health insurance provider simply by which videos they viewed.
How passive YouTube network traffic analysis works
Imagine an observer standing outside your house and observing all the packages being delivered to your door.
Even though each package has a different size, shape, and weight, an observer could match them to a catalogue of known packages and conclude what you’ve ordered, even if they never opened your packages.
When you’re using YouTube, each package not only has a unique signature—it also carries the IP address of both the sender (YouTube) and receiver (you). With these IP addresses, an observer can determine whether a package is associated with a YouTube video—along with your identity.
This observer could be a hacker who controls the router at your local coffee shop, the administrator of your campus Wi-Fi network, or your ISP.
Dubin: “I might even be able to guess what video you’re watching after around 30 to 40 seconds of watch time.”
Dubin’s research even applies when you watch only part of a video—and potentially in real time, too. “I have a different demo showing that I can predict in real time part of the video, as well. However, the accuracy of this algorithm is not finalized.” He estimates that it takes around 30 to 40 seconds of watch time to determine which video you’re watching.
Should we be worried about video mass-monitoring?
Yes and no. While surveillance at this point is possible, it’s costly, as the observer would need to compile a list of all the YouTube videos they want to identify and then analyze them one by one. This may sound onerous, but it need only be done once for each video of interest.
Variable network conditions could pose additional challenges, as packet loss and network delays create uncertainty. However, Dubin showed that he can still achieve a very high prediction success rate under these conditions.
Because the pre-recorded patterns only probabilistically match with the observed ones, a very large data set would likely contain some false matches. Dubin explained that while his study observed zero false-positive with a sample size of 2000 videos, drastically increasing the amount of titles may increase this number because “the Bit-Per-Peak feature may not be 100% unique.”
While this analysis could theoretically apply to other services and types of data as well (think Netflix, Facebook, or Spotify), Dubin won’t speculate about which other services could be vulnerable. But he says he may be planning his next research projects around services such as these.
How to protect your YouTube activity from being tracked
While YouTube theoretically could add obfuscation to their videos, Ran Dubin has advice on how you can protect yourself today:
“You can use VPN [or] you can use Tor networks to make identification much harder.”
Using a network like Tor or a VPN removes the immediate tool of identification: your IP address. By using a VPN, an observer would still be able to see which video was watched from the VPN server, but that traffic would be mixed in with hundreds of other users’ traffic, thwarting the ability to determine who was watching and from where.
Going back to the package metaphor, a VPN or Tor essentially creates a reshipment warehouse to which all packages are addressed and sent. Inside, they are accumulated, repackaged, and the occasional stuffing is added for further obfuscation. As the repackaged goods are sent to your home, an observer can no longer make a guess as to what is inside or who sent the packages.
Your ISP, or any other observer between you and your VPN provider, would see even less information. Due to obfuscation measures applied by modern VPN apps, your traffic patterns would no longer match the ones they may have pre-recorded, rendering the data they collect from you meaningless.
Beware of your metadata!
Even encrypted data carries along metadata. When you stream a YouTube video over HTTPS, this metadata comes in the form of timestamps, IP addresses, video size, video length, and—as Dubin has shown—the pattern with which the data gets transmitted.
Proxy networks like the Tor network or VPNs can help strip that metadata by either obfuscating it or by routing it through layers of proxies.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN















Comments
Great arcticle and great research!
Amazing. Big Brother is watching!
Nice