Why software security audits matter

Software is at the heart of how most organizations run today. It keeps things moving, helps teams work efficiently, and connects businesses with their customers. But as useful as software is, it also comes with risks, especially as cyber threats become more advanced and widespread.
Just one overlooked vulnerability can lead to serious issues, like data breaches, service outages, or damage to your reputation. That’s why software security audits matter. They help uncover hidden weaknesses in code and systems before attackers have a chance to exploit them.
In this guide, we’ll break down what software security audits involve, the different types you can run, and the key benefits they offer.
What is a software security audit?
A software security audit is a security-focused review of one or more pieces of software. It’s like an examination or inspection of software, with the primary objective of looking for any possible vulnerabilities that hackers or other bad actors might be able to exploit. In other words, it’s a way of finding out how secure software is.
Why are software security audits important?
Software security audits are absolutely crucial in this day and age, where cyber threats and attacks are increasingly prevalent and dangerous. Particularly in the world of business, and even more specifically in fields where compliance is of the utmost importance, audits provide valuable insights.
This is arguably more important now than ever before, as many businesses are becoming more and more dependent on various forms of software. Remote work is on the rise, leading to more frequent cyberattacks, while businesses now have larger networks, more connected devices, and a greater reliance on cloud platforms than ever before.
It’s worth noting, too, that the vast majority of software has at least some sort of weakness. Without audits, these issues could go unnoticed by users and exploited by hackers, possibly with devastating consequences.
Who needs a security audit?
Businesses that handle a lot of sensitive data or operate in industries with strict regulations about data privacy and security, like healthcare, finance, and the legal sector, have a particularly great need for security audits. They help such businesses remain compliant with all relevant regulations and mitigate the risk of data breaches, hacks, etc. This also has knock-on benefits for reputation, trust, and more.
Software developers, too, need to engage in application security auditing during the development stages of the programs they make. Thorough audits prior to release help to save on post-release patching and update costs, as well as help the developer’s reputation in terms of providing secure, trustworthy applications.
Key benefits of conducting a software security audit
There are numerous benefits to the software audit process, which only serve to highlight how important and valuable it can be.
Reduce vulnerabilities before they’re exploited
As explained above, the main goal of software security auditing is to spot weaknesses in software. This allows the users of those apps or their developers to take action if and when any issues are discovered. It’s usually much better to spot a flaw and fix it early on than have to deal with the consequences of that flaw being exploited.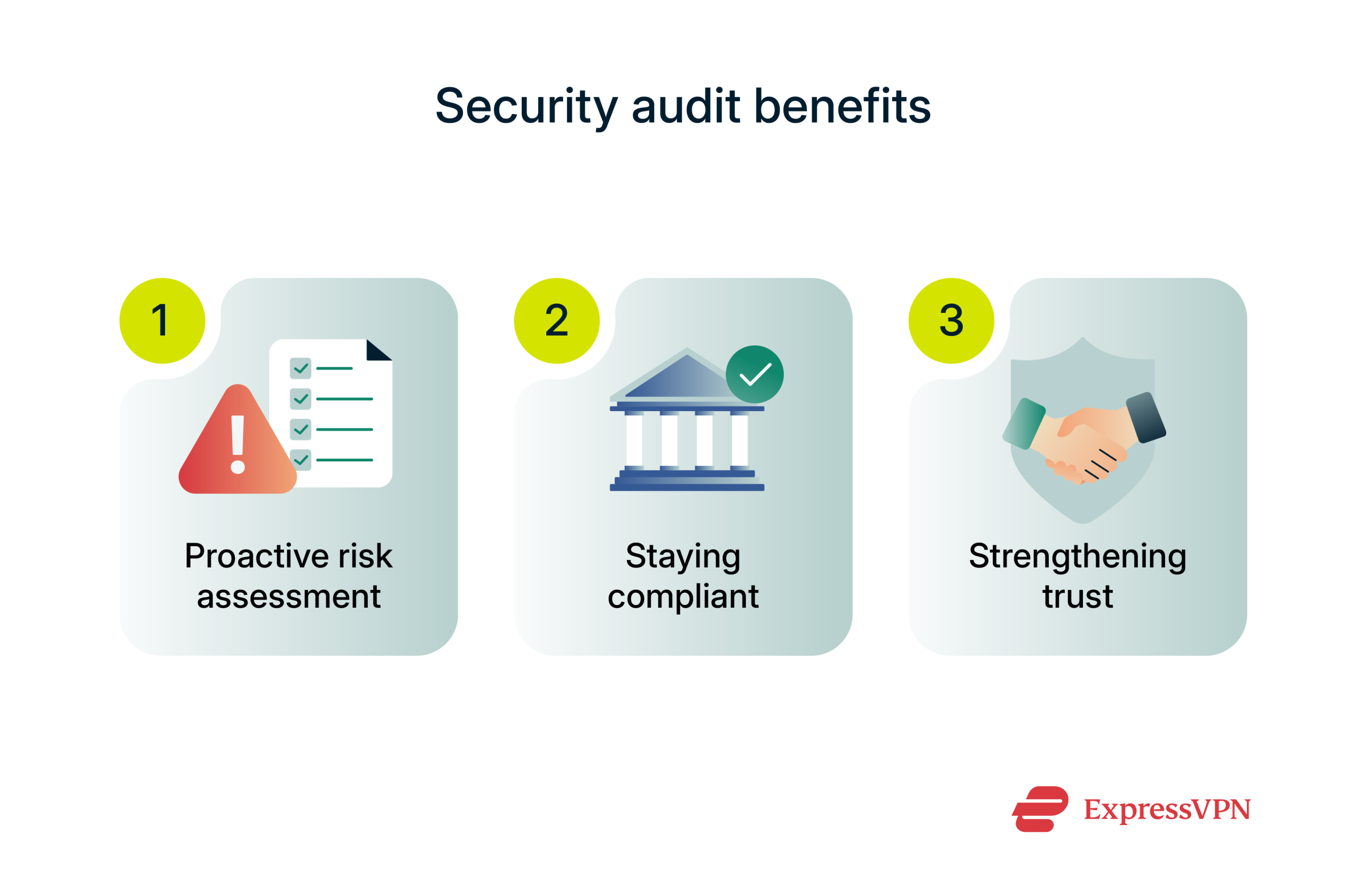
Meet regulatory and compliance standards
Companies that have to abide by strict regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), especially need to ensure that the software they use to handle sensitive data is secure. Otherwise, they risk serious legal consequences and financial penalties.
Improve customer trust and business reputation
The likes of data breaches and leaks can be devastating to a company’s reputation. There have been numerous high-profile examples of this in the past, with even some of the biggest and best-known tech brands experiencing losses in sales and customer loyalty after suffering data leaks.
To avoid such losses, organizations have to take steps to minimize the risks in the first place. Again, this is what software security auditing is all about. It helps firms maintain their defenses against data losses, which should, in turn, assist in fostering customer trust and loyalty.
Types of software security audits
There are numerous types of security audits organizations can carry out to assess the strength of their software. Here’s a closer look at some of the most common methods.
Static code analysis
Static code analysis examines an application’s source code without executing it, identifying vulnerabilities, bugs, or policy violations early in the development cycle. It’s commonly used by developers and security teams to improve code quality and reduce security risks before deployment.
Dynamic testing (DAST)
DAST evaluates applications in their running state, identifying vulnerabilities that only appear during execution, such as input handling errors or authentication flaws. It’s often used to test applications from an external attacker’s viewpoint.
Penetration testing
Penetration testing involves ethical hackers simulating real-world cyberattacks to uncover vulnerabilities across software, networks, or systems. Unlike code-focused testing, pen tests often target the full attack surface, including misconfigurations and exposed services.
There are several types of penetration testing, including:
- Black box: This is when the testers, or “ethical hackers,” attempting to exploit the software have no prior knowledge of how it works.
- White box: This is the opposite of black box; the testers have full internal knowledge of the system.
- Gray box: A mixture of the other two methods, in which the testers have some knowledge of how the software works.
During a typical penetration test, testers can look for weaknesses, like open ports, to find gaps in the software that they can exploit. At the end of the test, they may produce a report of their findings, evaluating the relative strengths and weaknesses of the system and providing recommendations on how to resolve any issues identified.
Security compliance audits (e.g. SOC 2, ISO 27001)
There are also more comprehensive forms of software security and compliance audits that evaluate an organization’s entire systems and processes against strict standards and criteria.
Examples include:
- SOC 2: A SOC 2 audit is based on the Trust Services Criteria of the American Institute of Certified Public Accountants (AICPA) and evaluates system security, availability, integrity, confidentiality, and privacy.
- ISO 27001: This audit measures an organization’s IT systems to ensure they comply with the requirements of the globally recognized ISO 27001 standard for information security management.
Common risks and vulnerabilities found in audits
As mentioned earlier, the majority of programs audited for the first time are found to have at least one weakness. These weaknesses can take numerous forms. Let’s take a closer look at some common examples.
Code injection
Code injection vulnerabilities occur when an attacker is able to insert and execute arbitrary code or commands due to insufficient input validation or insecure coding practices. Common forms include Structured Query Language (SQL) injection, where attackers manipulate database queries to access or alter data, and OS command injection, which allows execution of system-level commands.
These vulnerabilities can lead to serious consequences, such as unauthorized access to sensitive data, database manipulation, or remote command execution, potentially granting the attacker control over the underlying system.
Authentication weaknesses
Authentication is a critical part of program security, as it helps to control who can access the program and whatever data it contains. However, many programs have authentication weaknesses, which can include:
- Weak password policies: Applications may permit short, simple, or commonly used passwords, increasing the risk of brute-force attacks or credential stuffing. Lack of requirements for complexity, expiration, or rate-limiting can further exacerbate the problem.
- Hard-coded credentials: Sometimes, login information, such as usernames or passwords, is embedded directly in the source code or configuration files. If exposed through source leaks, these credentials can grant attackers persistent access to critical systems.
- Insecure recovery mechanisms: Poorly designed account recovery processes, such as predictable security questions or recovery links that don’t expire, can allow unauthorized users to reset passwords and hijack accounts.
- Lack of multi-factor authentication (MFA): MFA adds a crucial security layer by requiring a second form of verification, such as a code from a mobile app or a biometric scan. Unfortunately, many applications still do not support or enforce MFA, leaving them more susceptible to account takeover through stolen credentials.
- Default or unchanged credentials: Especially common in Internet of Things (IoT) devices and admin panels, using factory-default usernames and passwords can give attackers an easy way in, especially if these defaults are publicly documented.
Improper access controls
Access controls are also essential in many applications for managing which users have access to which features, functions, and files. Particularly in programs that are designed for business use in highly regulated industries, it’s important to have strong access controls, with clear user roles and privileges.
Despite their importance, access control mechanisms are often misconfigured or insufficiently enforced. Common issues include excessive user privileges (violating the principle of least privilege), lack of role-based access control (RBAC), or flaws that allow attackers to escalate privileges or access unauthorized data and functions.
Software security audit process: Step-by-step
Carrying out a comprehensive and efficient software security audit is a complicated process but becomes easier when broken down into simple stages. Here’s a look at the four key steps to follow to prepare for, implement, and learn from the software audit process.
Planning and scope definition
First, you need to think about the scope of your audit. Some organizations may only want relatively small checkups of their software security, while others will want to go much more in-depth. Defining the scope early on makes it easier to plan out the rest of the audit and choose the most appropriate testing methods, as well as set a timescale for the process.
Testing and evaluation
With the plan outlined, it’s time to put it into action. In this phase, your auditors will use the various testing methods and tools at their disposal, such as static and dynamic code analysis and penetration testing, to analyze and assess the strength of your software. This is the crux of the process, as it is where any issues with your program(s) should be identified.
Audit reporting and recommendations
At the end of the testing phase, auditors will typically produce a report of their findings. They’ll outline the tests they conducted, the results of those tests, and provide lists of any issues they uncovered along the way. They may also suggest various recommended actions for you to take to bolster your defenses and resolve the flaws found.
Remediation and follow-up
Upon receipt of the audit report, organizations should take the next necessary steps to correct any issues with their systems. Once their developers have corrected everything, a follow-up audit can be conducted to check that the new changes are effective and that all of the treated exploits are fully resolved.
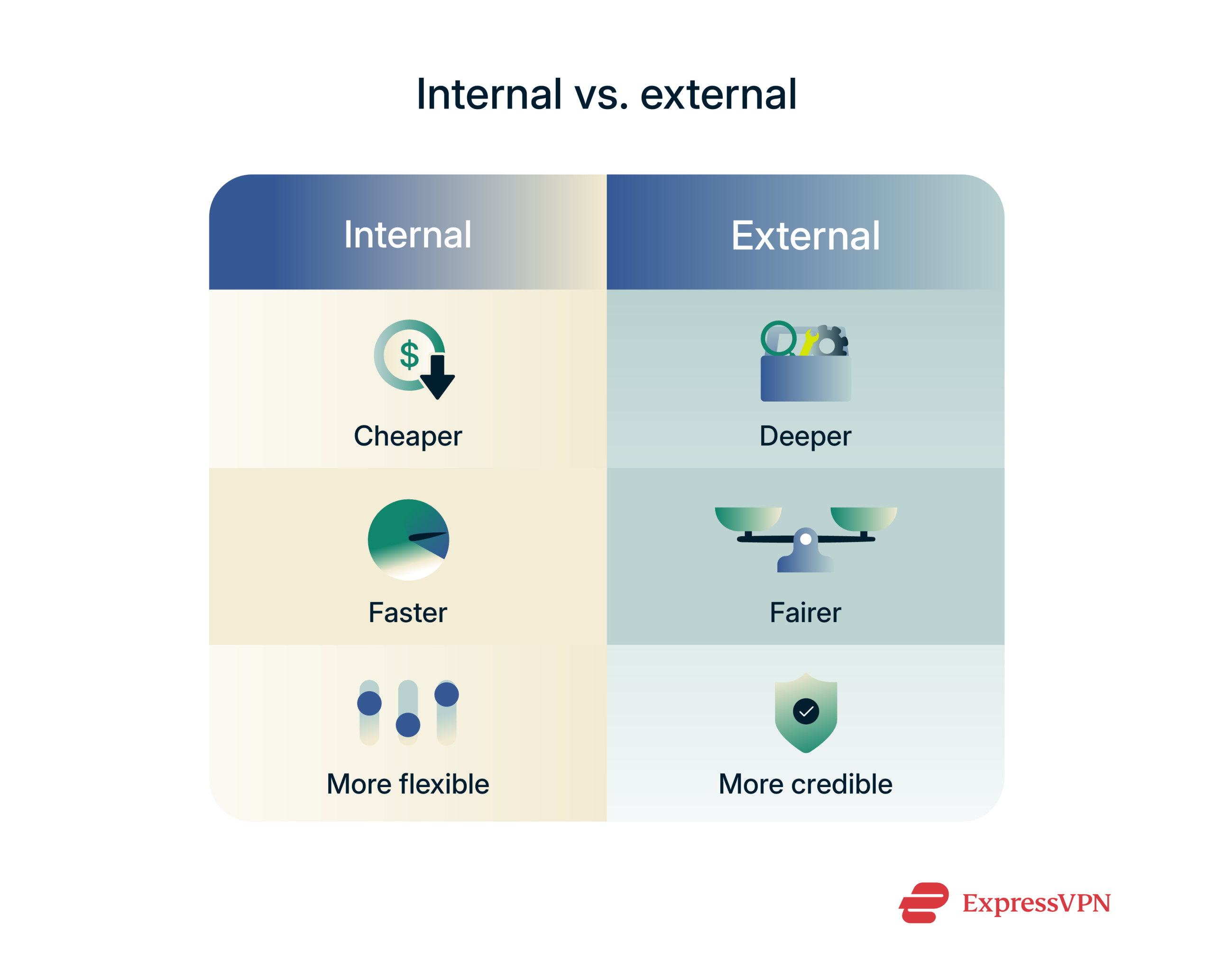
Internal vs. external security audits
We can divide security audits into two distinct varieties: internal and external.
Internal audits are carried out by an organization's own in-house tech experts or auditors to assess threats from within, while external audits are conducted by independent, third-party experts for an external, unbiased review.
There are advantages and downsides to both of these options, as well as ideal use cases for each.
Pros and cons of internal audits
Pros of internal audits include:
- Often more cost-effective: It’s usually cheaper to let your own in-house auditors carry out audits and assessments rather than hire an external firm.
- Rapid results: Third-party auditors may have backlogs of clients to help before they can get to you, so your own in-house team should be able to audit your software faster.
- Familiarity with the system: Your in-house experts should be fully familiar with the software you use, while external parties may need time to understand it.
- Greater control: With an internal audit, you’re in charge of how deep it is, which methods are carried out, and what the next steps are.
 On the downside, internal auditing presents the following problems:
On the downside, internal auditing presents the following problems:
- Possible bias: One of the most commonly cited issues with internal audits is that in-house teams may show bias toward the company, possibly overlooking issues.
- Lack of experience/expertise: This varies from organization to organization, but some in-house tech teams may not have the necessary expertise to conduct a thorough audit.
- Less credible: The results of internal audits are sometimes viewed as less credible than those carried out by third-party firms.
When to use external auditors
External auditors bring their own distinct benefits to the table compared to internal ones. External audits are often viewed with more credibility since they are conducted by external firms that have no ties to the company itself and will therefore assess the software without any bias. In addition, these firms may be more experienced in checking for security weaknesses.
Because of these benefits, organizations are better off using external audits for:
- Unbiased assessments: If you prioritize a complete, clear picture of your software security without any biased judgment seeping into the final report.
- Comprehensive audits: Third-party auditors will often provide the most in-depth, detailed looks at your software.
- Compliance: It’s often better to have a third-party audit report as proof of your compliance with regulations over an internal one.
Nevertheless, there are still some downsides with external audits that are worth keeping in mind, like their additional costs and the extra time it might take for them to be arranged and completed.
Integrating audits into the software development lifecycle (SDLC)
Security audits are not just to be used after a program has been completed and released. They should form part of the SDLC, with regular audits at key stages to help the final program be as secure as possible.
Benefits of early security integration
- Cost-effective: It’s often more cost-effective to carry out security audits and fix vulnerabilities early in a program’s lifecycle than to have to rush through big security patches and fixes later on.
- Reputation: Developers can suffer blows to their reputation and credibility if they release programs that are not fully secure. Testing and improving security through the development phase helps to avoid this.
- Compliance: If you’re working on an app that needs to abide by strict compliance requirements, it’s vital to make security part of the SDLC, as this will ensure your program meets all relevant rules and regulations at the time of release.
- Resilience: Making security a core pillar of the SDLC ultimately results in better, stronger, more resilient software that should better serve your users.
Tools that support continuous auditing
Various tools and solutions can support regular or continuous security auditing through the SDLC, including:
- Security information and event management: These collect and analyze security data automatically from a range of sources, giving a continuous and holistic view of the security landscape.
- Endpoint detection and response: These solutions constantly monitor endpoints to look for signs of malicious activity and help users record and respond to any security incidents.
- Vulnerability scans: Scanning tools can constantly scan systems and pieces of code to look for issues like vulnerabilities or misconfiguration.
- Penetration testing tools: These tools are able to do the work of “ethical hackers” themselves, carrying out real-world attack techniques against a system or piece of software to check how well it would withstand actual attacks.
How ExpressVPN conducts software security audits
Security audits are especially important for pieces of software that are supposed to keep users safe and secure, like VPN clients. For this reason, ExpressVPN takes auditing seriously, regularly engaging in both internal and external audits to look for and address any weaknesses within the software and maximize safety for customers around the world.
Internal security auditing practices
ExpressVPN conducts its own in-house audits and assessments of its software, policies, and new updates or changes before rolling them out to the public. These audits are designed to proactively identify potential security risks and vulnerabilities, ensuring that the software is both robust and secure before being used by customers.
Third-party external audit partners
Internal auditing can only go so far, which is why ExpressVPN regularly calls on the services of experienced external auditors to assist. The ExpressVPN software has, over the years, undergone multiple audits carried out by firms like Cure53 and Praetorian, looking at the design and implementation of ExpressVPN technology.
Public audit reports
ExpressVPN is also completely transparent about its third-party audits. It shares updates when new audits are completed so anyone can take a look through the third-party assessments to see how secure ExpressVPN actually is:
- The third audit of ExpressVPN’s TrustedServer technology by KPMG
- The fourth audit of ExpressVPN’s Lightway protocol by Cure53
- The third audit of ExpressVPN’s Lightway protocol by Praetorian
- The second audit of ExpressVPN browser extension by Cure53
- Nettitude’s audit of ExpressVPN’s Windows app
Best practices for running effective software security audits
To help you make the most of your software security audits, consider these recommended practices:
Use a framework (e.g., OWASP, NIST)
Frameworks provide structure to the software’s secure auditing process. They provide clear rules and guidelines to follow, helping you plan out your audit and implement the necessary testing steps to get the results you are looking for. Example frameworks to consider include the National Institute of Standards and Technology (NIST) and Open Worldwide Application Security Project (OWASP) frameworks.
Document everything
Keeping a written record of the entire audit process is very helpful for various reasons. Firstly, it could prove to be valuable evidence when it comes to demonstrating to regulatory bodies that your audit was thorough enough to meet their guidelines. It also lets you review the entire process at the end and possibly spot any areas that weren’t fully explored or could use more attention next time.
Make it a continuous process
Software security auditing shouldn’t be considered a one-off process to do once a year. Instead, it’s much better to take a continuous approach to auditing, using the tools and systems available to you to regularly review your software situation, constantly seeking out issues and ways to strengthen your position.
Conclusion: Why every software team should prioritize audits
Overall, security audits should always be a top priority for any team, as they can help you spot and resolve errors before they create any major problems, helping with compliance, cybersecurity, and credibility for your business. Without audits, you may have several major weaknesses within your system, and it could be only a matter of time until they are used against you.
FAQ: Common questions about software security audits
How often should you perform a software audit?
What does a typical audit report include?
What are the two types of security audits?
How much does a software security audit cost?
How do you conduct an IT security audit?
What is an example of a security audit?
What does a full software security audit cover?
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN

















Comments
Are there any plans to conduct any third-party audits in 2024?
Hello, yes there are. We can't say much yet regarding timeline and area of focus, but we'll be completing some soon.